
This Jammer Wants to Block Always-Listening AI Wearables. It Probably Won't Work
Deveillance's Spectre I, developed by a recent Harvard grad, wants to give people control over the always-on wearables surrounding their lives. The problem? Physics.

Deveillance's Spectre I, developed by a recent Harvard grad, wants to give people control over the always-on wearables surrounding their lives. The problem? Physics.
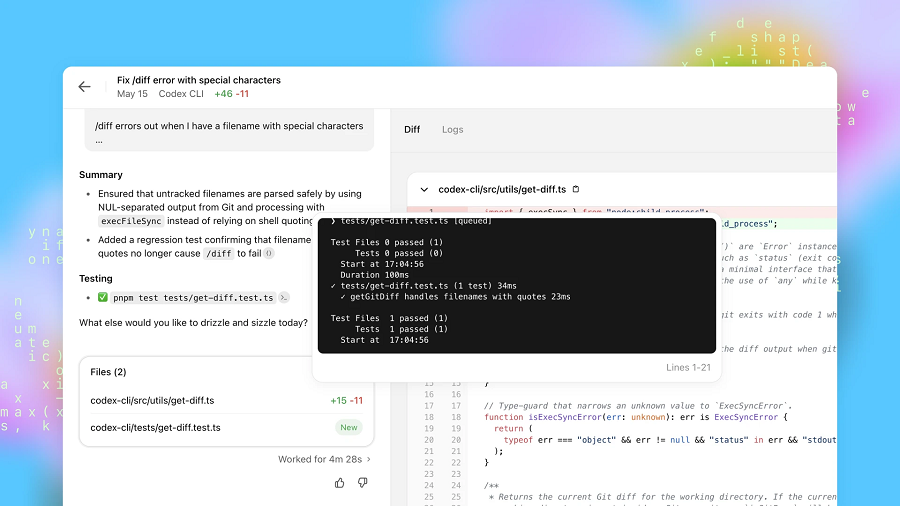
OpenAI Group PBC today debuted Codex Security, a new tool in its Codex programming assistant that can help developers find and fix code vulnerabilities. The launch comes two weeks after Anthropic PBC introduced a competing product. Claude Code Security can an…
AI-assisted cyberattacks are accelerating reconnaissance and techniques such as password spraying against exposed devices. Learn how attackers are using AI prompts to automate attacks and the steps organizations should take to protect their network.

OpenAI introduced an application security agent designed to build deep context about the user’s project to identify complex vulnerabilities and minimize false positives. The agent, Codex Security, is now in research preview, the company said in a Friday (Marc…

Palantir's stock had its best week since August and outperformed all of its large-cap tech peers after the U.S. attacked Iran.

Market data predicts that by 2027, more than 50% of business decisions will be augmented or automated by AI-driven decision intelligence platforms. That shift reflects a structural transition from insight generation to outcome orchestration. In the latest epi…

Iran vs Everyone: 2FA-Bypass Phish, APT41 Drive, iOS 0days, Josh Marpet, and More on the Security Weekly News Visit https://www.securityweekly.com/swn for all the latest episodes! Show Notes: https://securityweekly.com/swn-561

More than three dozen police officers will soon be equipped with body cameras in a move Winnipeg's police chief says will help investigations and boost accountability.

Over three dozen police officers will soon be equipped with body cameras in a move Winnipeg's police chief says will help investigations and boost accountability.

Open-source software has become the backbone of modern application infrastructure. From distributed databases to event streaming platforms, technologies such as Apache Cassandra, Apache Kafka and PostgreSQL increasingly power the digital services that organiz…

Anthropic PBC has shared an update about its artificial intelligence safety feud with the Pentagon. In a Thursday blog post, Chief Executive Dario Amodei stated that the company has been “having productive conversations” with defense officials. He also addres…

Anthropic PBC has shared an update about its artificial intelligence safety feud with the Pentagon. In a Thursday blog post, Chief Executive Dario Amodei stated that the company has been “having productive conversations” with defense officials. He also addres…
Strategic Action Aimed at Regaining Compliance with Nasdaq’s Minimum Bid Price Requirement and Protecting Continued Listing Status YOKNEAM ILLIT, ISRAEL,...
Dallas, TX, March 06, 2026 (GLOBE NEWSWIRE) -- Mangoceuticals, Inc. (NASDAQ: MGRX), a company focused on developing, marketing, and selling a variety of health and wellness products via a secure telemedicine platform under the brands MangoRx and PeachesRx, an…

The Curve Finance team notified the team behind the PancakeSwap DEX that it needs to acquire a license before using code developed by Curve Finance.

The former Secretary of D.H.S. faced criticism for misspending funds, prioritizing her own self-promotion, and reflexively defending even the most brutal acts of the Trump Administration’s deportation efforts.

Once again, artificial intelligence dominated the buzz at this year’s MWC Barcelona, formerly called Mobile World Congress. From smartphones to satellites, networks to applications, no vendor or service provider could resist the lure of AI. My challenge: Sort…
BARCELONA and KYIV and NEW YORK, March 06, 2026 (GLOBE NEWSWIRE) -- Kyivstar Group Ltd (“Kyivstar Group”; Nasdaq: KYIV;KYIVW), the parent company of JSC Kyivstar, Ukraine's leading digital operator and part of VEON Group (Nasdaq: VEON) announced at Mobile Wor…

We found a fake Google Meet update that enrolls the victim's Windows PC in an attacker's device management system.
Gymnasium environments for cybersecurity threat detection with continual learning

IntroductionThreat actors often take advantage of major global events to fuel interest in their malicious activities. Zscaler ThreatLabz is diligently tracking a surge in cybercriminal activity that capitalizes on the elevated political climate in the Middle …

In a co-ordinated public-private operation between law enforcement agencies and cybersecurity industry partners, Tycoon 2FA - one of the world's most prolific phishing-as-a-service platforms - has been dismantled. Read more in my article on the Hot for Secur…
The games continue in Italy. We'll show you where to watch the Winter Paralympics online in 2026.

Our main thesis coming out of MWC 2026 is that the telecommunications industry is staring at a once-in-a-generation infrastructure reset. Carriers poured billions into 5G spectrum, fiber expansion and network modernization on the promise that faster networks …

Modern networks improve performance, resiliency, security and flexibility. These gains translate into measurable direct and indirect returns for the business.